I noticed that a lot of people were bypassing my proxy using Firefox Portable and other standalone browsers. I am using a proxy installed on a machine that is not directly attached to my default gateway, so I have them pick up the proxy address from wpad, and lockdown the proxy settings page in IE through Group Policy.
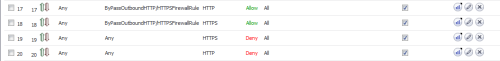
A simple solution to people bypassing your proxy, is to put an entry in your firewall to only allow HTTP and HTTPS traffic that originates from your proxy server. If you’re not administering a very large network this is ideal. Another advantage, since it is not specific to just Firefox, it will allow you to catch any browser that users throw at it and force them to put in proxy settings to use the internet. This also solves the problem if they try to get around the proxy by modifying their “auto detect proxy” settings. Since Group Policy cannot lockdown the proxy editing page of every browser, and people always find clever ways to install the multitude of internet browsers out there, this will not allow them to simply bypass it by turning the “don’t detect proxy” setting off . Here’s what the entries look like in a Sonicwall router to allow only http/https traffic that comes from your proxy (the proxy server in this example is called flserver4.)
Once you have a rule like the above setup, you can add a few exceptions in for your servers, etc. by placing an “allow” for those addresses with a lower priority than the deny. In the example above, I created an Address Group and can add IP addresses/hosts to it whenever I need. I would put an allow entry in where the source is my Server IP, the destination is ANY, and the service is Http/Https, at a priority of 17/18, which would process before the deny. To make it easier you can create a Service Group containing both HTTP and HTTPS ports so you don’t have to put every exception in twice as well as the address group to contain the hosts you would like to allow this way you do not have to create an entry for every ip address.
Obviously, The best way to use a proxy is to use two nics and place the server/device in front of your router, or use a content filtering solution that is installed on the router itself since all traffic leaving must go through this server/device to get out. Sonicwall has one, Cisco has one on a certain series of routers. However, if you have a proxy working on a standalone server that is not installed in front of your gateway so that all traffic has to pass through it, then the above solution should suffice. Everyone out there has a different setup so this will help when you do not have the luxury of having this type of setup.
There is a also an ADM out there that allows you to configure Firefox through Windows Group Policy, however, since Firefox standalone is not actually installed on the machine and does not contain registry entries, I’m not sure that this will work, so you might want to investigate that. Another person has a great writeup on how to create your own. If you need to enforce more than just proxy settings then you should take a look at it.
Here’s another writeup I had on autoconfiguration setup a little while ago that addresses how to set it up and contains links at the bottom on troubleshooting and concerns with using wpad.